Web Architecture
What you See When You Visit a Webpage1
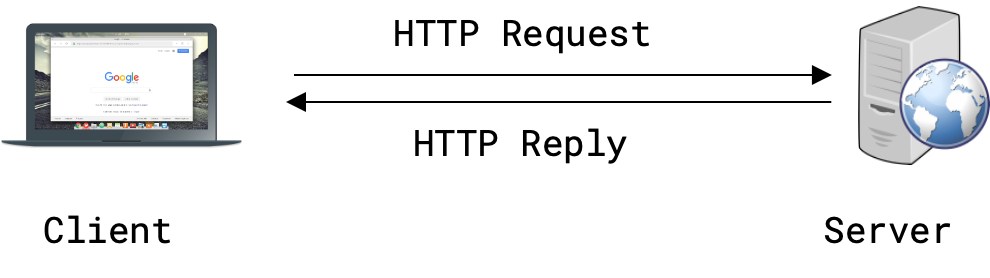
What is Happening When You Visit a Webpage
When you visit a webpage, it looks like you make a request to HTTP and then get a reply. But many things are happening along the way!

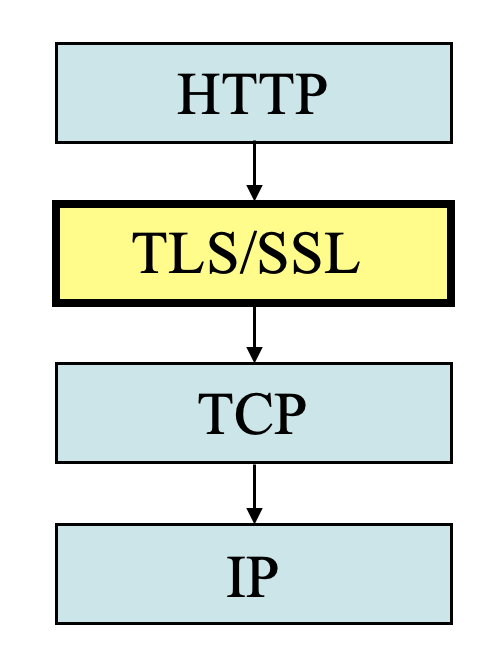
Web Transport Security: SSL
TLS (Transport Layer Security) is a protocol that provides an end-to-end encrypted communication channel. You may sometimes see SSL (the old, deprecated version of TLS).
End-to-end encryption guarantees that even if any one part of the communication chain is compromised (for example, if the packet passes through a malicious AS), no one except the sender and receiver can read or modify the data being sent.
SSL/TLS includes protocol mechanisms to enable two TCP users to determine the security mechanisms and services they will use.
Where is TLS/SSL useful?
- Online commerce
- Varying risk between client and server (customer and retailer)
- Web services
- Secure password authentications!
- Session establishment for internet applications (e.g. VoIP)
- VPN connections
HTTPS (HTTP Secure) refers to the combination of HTTP and SSL to implement secure communication between a Web browser and a Web server.
Uniform Resource Identifier
- Essential metadata to reach/find a resource
- More general than URL! (Uniform Resource Locator)
- Answers the following questions:
- Which server has it?
- How do I ask?
- How can the server locate the resource?
Latest definition in RFC 3986 (January 2005)
URI – Syntax
<scheme>:<authority>/<path>?<query>#<fragment>
- scheme: The protocol to use to request the resource
- authority: The entity that controls the interpretation of the rest of the URI. Usually a server name
<username>@<host>:<port>
- path: Usually a hierarchical pathname composed of “/” separated strings
- query: Used to pass non-hierarchical data
- fragment: Used to identify a subsection or subresource of the resource
URI – Syntax
<scheme>:<authority>/<path>?<query>#<fragment>
Examples:
ftp://ftp.ietf.org/rfc/rfc1808.txt
mailto:akaprav@ncsu.edu
https://example.com/test/example%3A1.html?%2Falex
URI has Reserved Characters, so you can type in things like <space> using %20 (that’s why the example above has the %2F)
URI – Absolute vs. Relative
- URI can specify the absolute location of the resource
https://example.com/test/help.html- Or the URI can specify a location relative to the current resource
- Relative to the current network-path (scheme):
//example.com/example/demo.html
- Relative to the current network-path (scheme):
- Relative to the current authority:
/test/help.html - Relative to the current authority and path:
../../people.html - Context important in all cases
http://localhost:8080/test
JavaScript
JavaScript is a programming language that runs in your browser. It is a very powerful language–JavaScript can arbitrarily modify most HTML or CSS on a webpage. Almost all modern webpages use JavaScript.2 Like CSS, you can also include external JavaScript files in your HTML or code can be embedded into HTML pages directly.
Webpages can include JavaScript in their HTML to use dynamic features like interactive buttons, or having a login (see gif below). When the browser parses this HTML element, it automatically fetches and executes the JavaScript before continuing to parse the rest of the HTML.
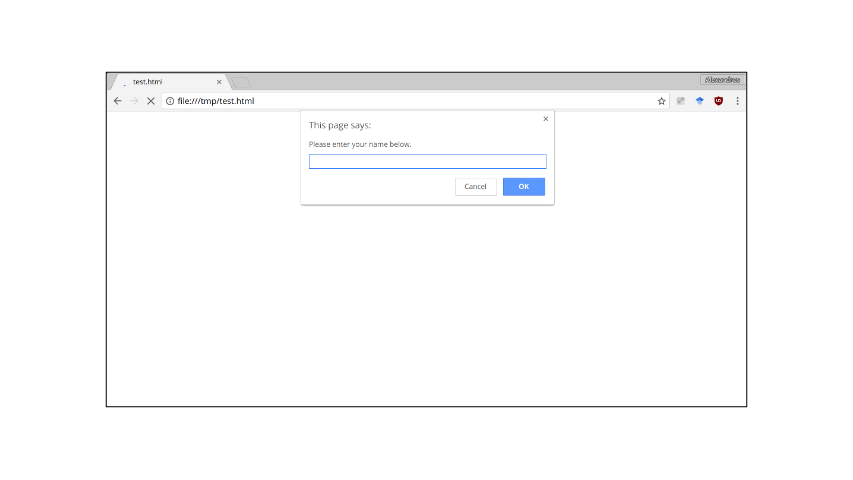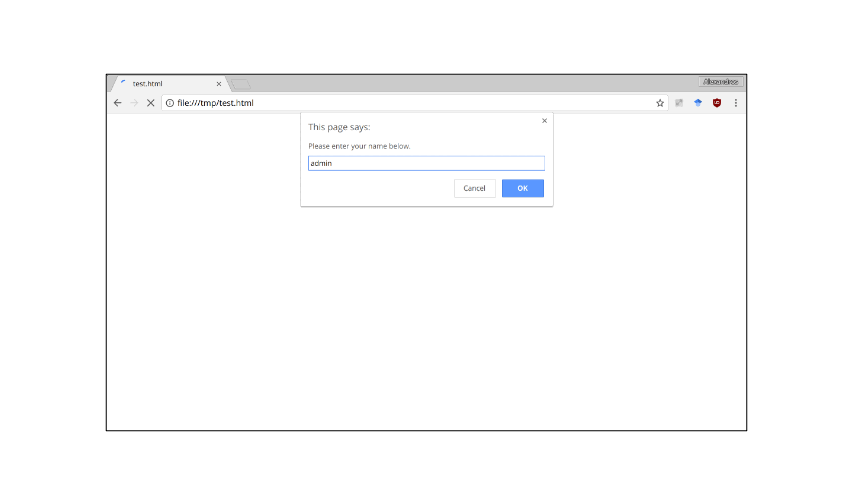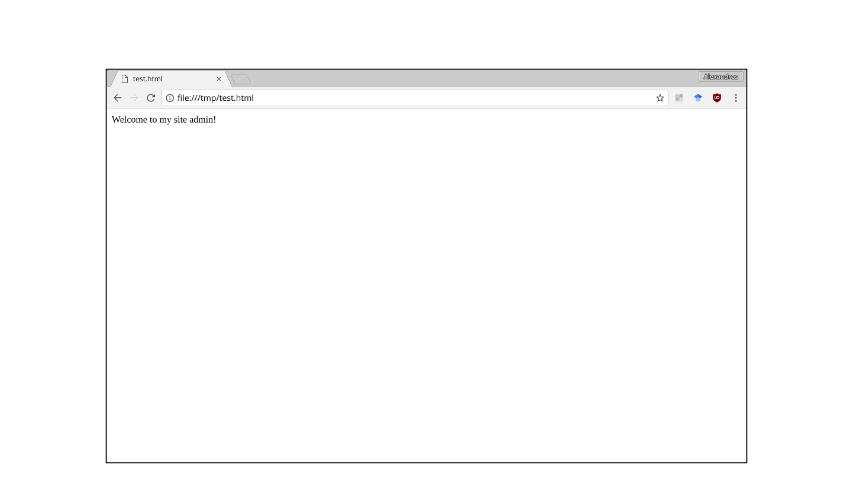
Security Concerns
Drive-by download
- Web based exploits that target browsers and their plugins
- Usually based on JavaScript
Zero-day exploits
- February 2 2015 – Adobe Flash – CVE-2015-0313
- March 12 2015 – AdobeFlash- CVE-2015-0332 – CVE2015-0342
- April 14 2015 – AdobeFlash – CVE-2015-0346 – CVE- 2015-0360 + more
- 26 October 2016 – Adobe Flash – CVE-2016-7855
- 11 April 2017 – Adobe Flash – CVE-2017-3058 CVE-2017-3064
Adobe finally End-of-Life’d Flash in 2020!
Browser extensions
- HTML + JavaScript
- Modify and enhance the functionality of the browser
- Have access to a privileged API

What can a malicious extension do?
- Anything malicious that you can do with JavaScript having access to the visited page, the web requests, the browser’s cookies
- Inject advertisements
- Keylogger (only in the visited page)
- Affiliate fraud
- Steal credentials