Malware
Malware is a portmanteau of “malicious software”123. We’ll go through some examples of types of malware. Note that there is overlap between types of malware — ransomware could be a trojan or a virus!
Malware can target any type of computer system, e.g.,
- PCs and servers
- mobile devices
- process control systems
How You Can Get Infected
- E-mail attachments
- Example: files with malicious scripts embedded: Microsoft Warns of Tax-Themed Email Attacks Using PDFs and QR Codes to Deliver Malware
- Example: via social engineering
- Instant messaging links and attachments (such as on Discord or Telegram)
- Pirated Software (Trojans are often embedded in illegal ‘warez’)
- Infected USB drives or other removable media
- file downloads (many backdoor Trojans are embedded with other files)
- Unreliable download sources
- Browser extensions
- File-sharing applications
- Program installers that can be downloaded from the internet may “bundle” other software into the installation.
- Fake mobile apps from third-party app stores
- Clickfix, where the visitor to a hacked or malicious website is asked to distinguish themselves from bots by pressing a combination of keyboard keys that causes Microsoft Windows to download password-stealing malware.
Avoid running programs you don’t need to prevent unwanted access to your computer. When installing new software, you must read each prompt the installer puts on the screen to make sure that software is not being installed inadvertently.
Malware that Spreads
- Virus — Malicious code that is spread through infected programs or files (e.g., Excel macros or PDF files)
- Worm — Directly uses a network service to spread itself. Typically exploits a vulnerability in a target to execute code that then exploits more systems
- Trojan Horse — malicious software embedded in what appears to be a useful program
Typically, worms are self-propagating and spread without user interaction, whereas viruses require users to do things like copy an infected file.
How to protect yourself from viruses
- Enable antivirus software and keep it updated (any anti-virus from the approved list, including Defender).
- Keep your operating system and software up to date
- Don’t open unexpected file attachments, even from friends. If in doubt, ask the sender.
- Avoid running programs or downloads from unknown sources.
- Avoid opening unrecognized attachments, especially those that do not come through a mail provider that screens for malware
- NCSU’s Gmail screens attachments for malware, though this is not a guarantee.
- If you know the person who sent you a file, but were not expecting it, you may want to contact them before opening it. Many viruses automatically send themselves out to addresses found in files on an infected computer.
- Before running a download from an unknown site, or opening an e-mail attachment, always scan it to ensure that it is not infected. If you do not know the source of a file, do not open it.
Malware that Hides
- Rootkit: A secret program designed to give back door privileged access to a system. Obtains “root” privileges, and often embeds itself in kernel code
- Bots and Botnets: A bot is a host, or computer, that is infected with malware that accepts remote commands from an attacker. A botnet is a network of exploited hosts controlled by a single party.
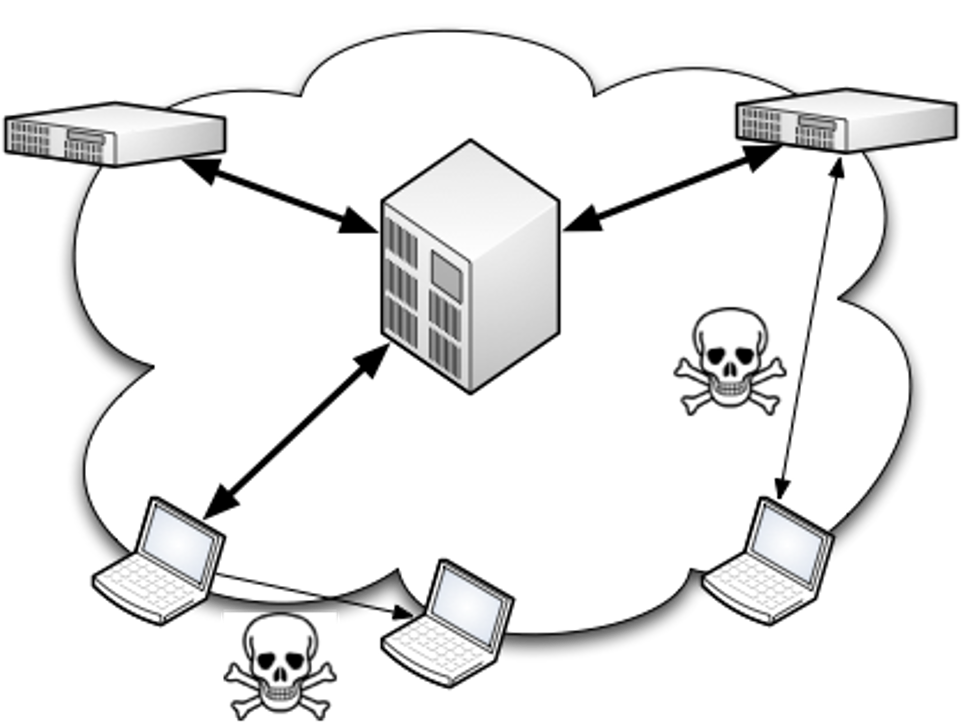
- Backdoor is a way to access a device bypassing normal entry points and access control. It allows ongoing stealthy remote access to a machine, often by enabling a network service. A backdoor program contacted via a backdoor may be used for malware installation and updates. These may come from program flaws or be intentionally built in by the developer.
Ransomware/Spyware
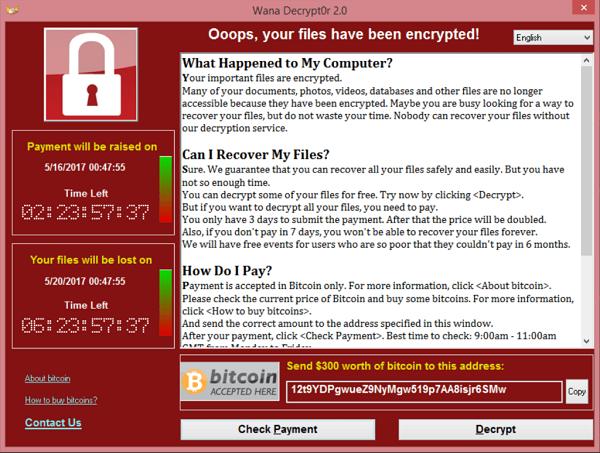
- Ransomware is malware designed to extort the user in exchange for access to something of value. Often in the form of “Pay or I’ll post your private data to the Internet.” Sometimes also referred to as “Scareware”. A common form is a fake anti-virus program that claims you have many viruses and must pay for the full version to get rid of them.
- Spyware: Focused specifically on gathering information about you. Think: data mining.
Spyware allows an attacker to gain remote access to a target’s data without the user knowing. Data includes messenger logs, photos, files, and contacts. Attackers can also do real-time surveillance, for example, by accessing the device’s microphone and cameras.
Attacks can relay the data to advertisers or other interested parties. Spyware can infect a computer as a software virus or as the result of installing a new program. If a user knows they’ve installed a data collecting program and understands what data is being collected and with whom it is being shared, then it is not strictly considered spyware.
Spyware and adware can cause many recognizable problems on infected computers, such as slow computer function, jumpy internet, and altered home pages in the web browser. While spyware and adware can affect any OS, Windows users are the hardest hit. This is due to the fact that Windows is the most widely used OS across the world.
You may have seen internet ads claiming that your computer is infected with spyware or viruses and asking you to click for a “free scan.” Unwary users may click on these ads, leading to a download that will infect the user’s computer with malware, all while telling the user that it is removing threats from the computer. You should avoid clicking on such ads.
Keyloggers
- Software that records and send user keystrokes to an attacker, or
- Hardware of some small, inexpensive memory device plugged in between a keyboard cable and a computer
Could be used to get your password!
Drive-By Downloads
Simply visiting a web page can result in malware being silently downloaded and run on the user’s device without the user knowing about it!
Zero-Day Exploits
A zero-day exploit (zero-day) takes advantage of a software vulnerability that is unknown to the developers. The day a vulnerability becomes known is the first day, and the attack precedes that — that’s why it’s called zero-day!
Read this book to learn more about cyberwarfare, and zero-day exploits in particular!
(The link takes you to the library website)
References
