Phishing
Phishing relies on impersonating a trustworthy entity to steal information or credentials from users. The type of information stolen from phishing messages can be any type of personal/sensitive data. For example, social security numbers, credit card numbers, phone numbers, or login credentials. Phishing can take many forms, such as emails, messages, and even QR codes. Phishing overlaps with similar concepts like scams or fraud.
Specific Examples
- Example 1: You get an email from a professor’s unityID@yahoo.com, asking you to immediately run to the store to purchase gift cards, as they forgot to buy presents for their kids. They will not forget this and will reimburse you.
- Example 2: You get a text message stating that your bitcoin balance on totallyBitCoinWallet.notascam.com is 900 bitcoin. To sign in, use the password hunter2 and username lucky.
- Example 3: An email from a university address that just states, “call me 555-122-2222”
- Example 4: You scan a QR code on a parking meter; the website looks identical to what you are used to; however, the domain reads totallyParkingMeter.notascam.com.
- Example 5: You get a call from NCSU University; they tell you that you need to immediately change your password and that they can do it over the phone.
- Example 6: You are sent an invoice on your email, body just says “see attachment below” and the attachment is what appears to be a invoice.pdf.
- Example 7: An email claiming that NCSU needs to audit your financial records, or you will be forced to pay back your financial aid, you can either respond with your UnityID/Password or upload a PDF of a list of documents at the link provided.
Examples 1 and 3 are widespread scams that target academics, and example 2 is pulled from prior work that studied SMS phishing attacks. In all of the examples above, there is a sense of urgency, which is what these actors rely on to steal your information or gain access to your machine.
Example 6 is a tricky one, on one hand, it could be a legitimate invoice, however, malicious PDFs never go out of style.
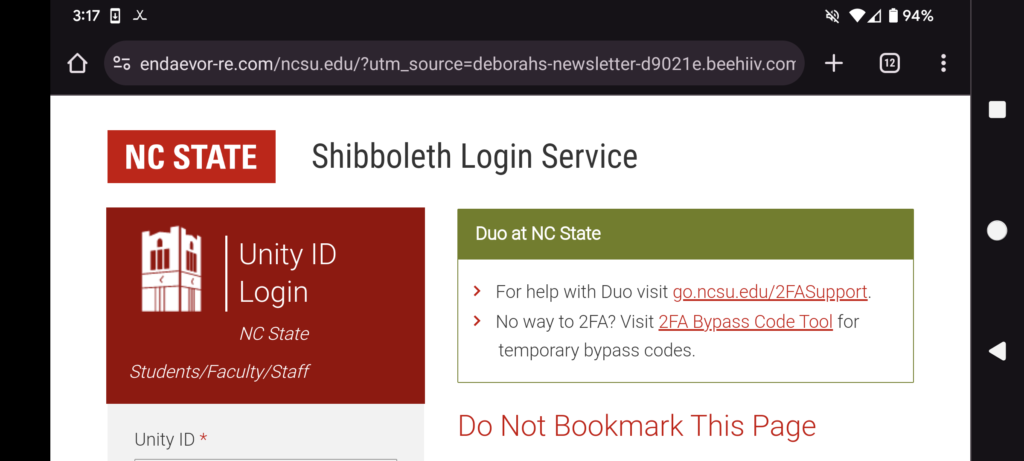
Pictorial Example
Here’s a site that looks identical to the shibboleth log-in page, but the URL is weird. It says things like “endaevor” and “deborah” and “beehiiv” instead of the usual shib.ncsu.edu. This is also on a phone, which tend to be more difficult to read URLs on, and therefore easier to be phished on!
Protect yourself from phishing attacks
- Remember that IT Staff will never ask you for your password
- Have 2-factor authentication enabled on as many accounts as you can
- Never re-use passwords
- Always look closely at the URL, especially on mobile, when entering personal information.
- Always look at the sender of an email. You may also try to ensure that it is Authenticated.
- Always report phishing emails if they make it through our SPAM filters!
- Avoid sharing personal information, under the pressure of urgency, if you do not know the entity on the other side.
- Never share 2FA codes over the phone. If someone on the phone claims that you need to accept a 2FA push notification, do not do so and change your password immediately.
- Never trust calls that demand the ability to remote into personal machines.
- Report suspected phishing attempts following these instructions.
These lists are not exhaustive, though we’ve tried to keep them full of recent examples. Phishers will change their tactics as time passes; ultimately, you should always exercise caution and guard personal information or machine access.
If you receive an email that does not look legitimate, do not respond or visit the link and do not provide your personal information to unknown sources. Please note that the university will NEVER ask you to send personal information through email.
1 Much of this page was authored by Aleksander Nahapetyan, as his research is in web security and phishing. ↩
