Networking Basics
- Networking is fundamentally about transmitting information between two devices1
- Communication is now possible between any two devices anywhere (just about).
Protocols
In life, protocols define the way we interact with other people. In computer science, protocols are rules that dictate the ways in which computers communicate with one another over a network medium2.
Examples of protocols include:
- HTTP (Hypertext Transfer Protocol): Used for transmitting web pages over the Internet.
- FTP (File Transfer Protocol): Used for transferring files between a client and a server. (FileZilla uses SFTP, secure file transfer protocol)
- TCP (Transmission Control Protocol): Data transport between machines across networks
- IP (Internet Protocol): Handles addressing and routing of packets between devices.
Encapsulation
Encapsulation in computer networking refers to the process of wrapping data with necessary protocol information before network transmission. Different protocols are used at each layer to add different wrapping to the transmitted data.
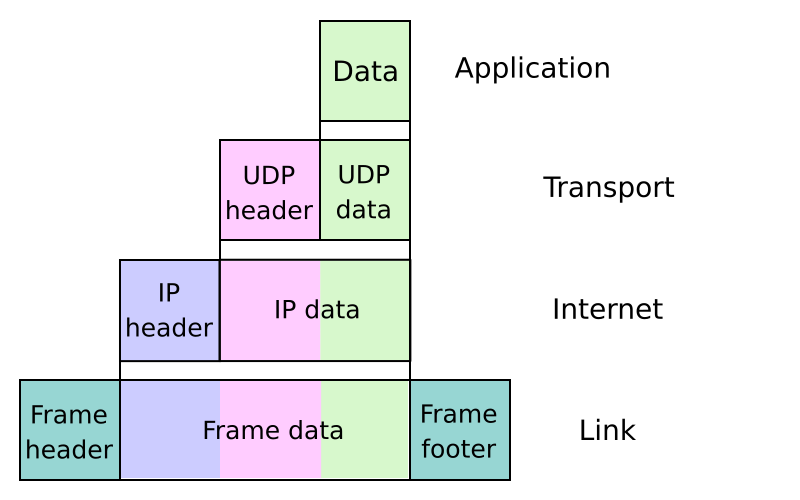
Figure 1: The data gets wrapped via multiple protocols.3
Simplified Encapsulation Description2
- Each layer processes messages (aka packets).
- When layer N receives data from layer N+1, it encapsulates the entire layer N+1 message within its own packet.
- Application layer just has data, transport wraps it with UDP (for example).
- Internet layer wraps with IP data
- Link layer adds frames.
- The process can be reversed once the data is received on the other end.
A good analogy for thinking about encapsulating with protocols is sending mail. You write a letter, which then gets encapsulated in an envelope. To properly process the envelope, you have to write the address that it’s going to and add a stamp (this is like adding header data).
| Layer | Example |
|---|---|
| Link Layer | Ethernet |
| Internet Layer | Internet Protocol (IP) |
| Transport Layer | Transmission Control Protocol (TCP) or User Datagram Protocol (UDP) |
| Application Layer | HyperText Transfer Protocol (HTTP) |
Connecting to the Network
- Each computer connecting to the network must be assigned a unique Internet Protocol (IP) Address. This allows other computers to know where a particular machine is located on the network and how to send information to that machine. The two types of IP addresses available are static and dynamic. Static IP addresses assign an unchanging, known address to the machine, and dynamic IP addresses are automatically assigned from a list of available addresses using Dynamic Host Configuration Protocol (DHCP).
- Internet Protocol version 6 (IPv6) is the current standard protocol used to route traffic across the internet. IPv6 addresses are 128 bits. The earlier protocol, IPv4, uses 32 bits. The new address space supports 2128 (about 3.4×1038) addresses, vs. the 232 supported by IPv4.
- IP addresses are usually written as 4 integers between 0 and 255, such as
128.32.131.10. Because the Internet has grown so quickly, the most recent version of the layer 3 protocol, IPv6, uses 128-bit IP addresses, which are written as 8 2-byte hex values separated by colons, such ascafe:f00d:d00d:1401:2414:1248:1281:87125
- IP addresses are usually written as 4 integers between 0 and 255, such as
- Network Address Translation (NAT) allows all computers connected to a router to share a single, public IP address. It then assigns a private IP address to all connected computers that it translates to the public address when sending the traffic to the Internet. NAT also acts as a firewall, and is widely used in home networks and small businesses.
- DNS (Domain Name System) allows you to use domain names instead of actual addresses to access a computer. The most common example of this is the address bar in your web browser. DNS is what allows you to access a page by typing “www.google.com” instead of the actual IP address for the Google search engine. DNS Servers keep track of the domain name and their associated IP addresses for ease of access. DNS can refer to Domain Name System or Domain Name Server.
Footnotes/References
- Content from CSC 474. Acknowledgments to William Enck, Brad Reaves, Micah Sherr, Patrick McDaniel ↩︎
- Reference: CS402 Saylor ↩︎
- Image shared with CC license. From Wikipedia. ↩︎
- Reference: CS402 Saylor ↩︎
- Reference: CS161, UC Berkeley, Ch 25. ↩︎